Configuration Example
# Enable LDAP authentication, default is false
Enable = true
# Hostname or IP address of the LDAP server, client will connect to this server for authentication
Host = '10.99.0.170'
# Port number of the LDAP server, default port is 389
Port = 389
# Starting point in the LDAP directory tree, all search operations will be performed under this base DN
BaseDn = 'dc=n9e,dc=com'
# User DN used to bind to the LDAP server
BindUser = 'cn=binduser,dc=n9e,dc=com'
# Password for the user binding to the LDAP server
BindPass = '1234'
# LDAP search filter for finding users, %s will be replaced with the actual username
AuthFilter = "(&(sAMAccountName=%s))"
# Whether to override user attributes, set to true means existing user attributes will be overwritten when synchronizing user information from LDAP
CoverAttributes = true
# Whether to override team settings
CoverTeams = false
# Whether to enable TLS connection
TLS = false
# Whether to enable StartTLS
StartTLS = false
# Default roles for users in the system
DefaultRoles = ['Guest']
# Default teams for users in the system
DefaultTeams = [21]
# User attribute mapping
[Attributes]
# Maps to displayName in LDAP
Nickname = 'displayName'
# Maps to mobile in LDAP
Phone = 'mobile'
# Email maps to mail in LDAP
Email = 'mail'
Detailed Explanation of Basic Configuration
Enable = true is the switch for LDAP configuration;
Host = '10.99.0.170' should be filled with the hostname or IP address of the LDAP server;
Port = 389 corresponds to the LDAP service port, default port is 389;
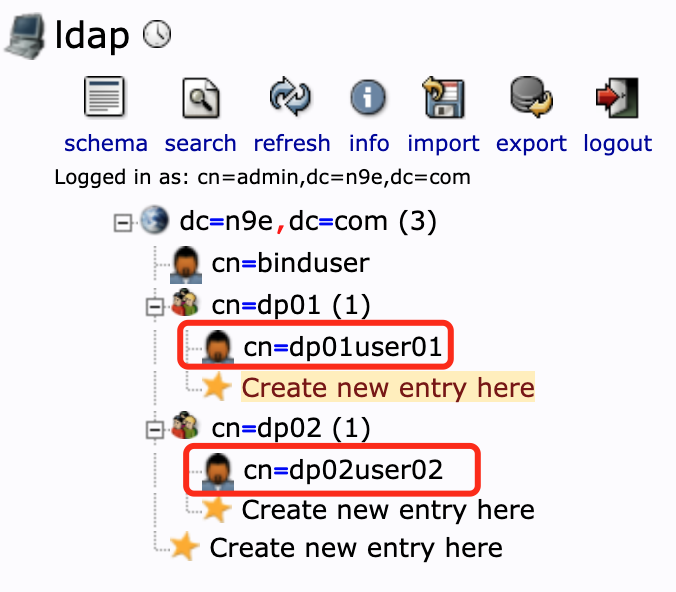
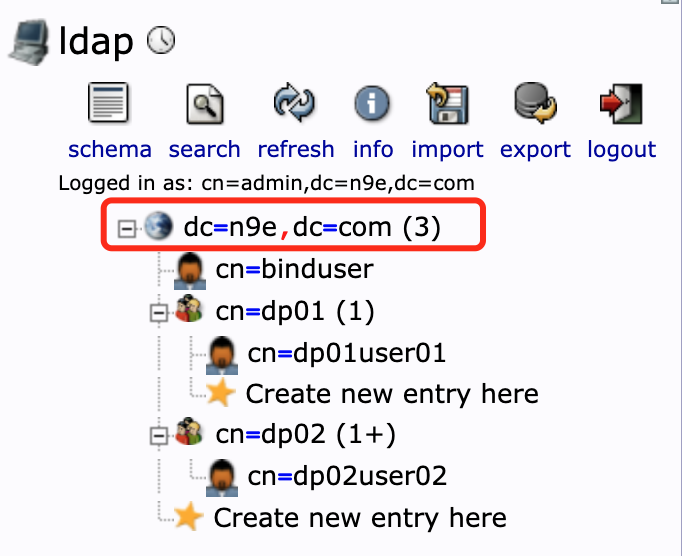
BaseDn = 'dc=n9e,dc=com' is the starting point of the LDAP service directory tree (as shown in the figure below);
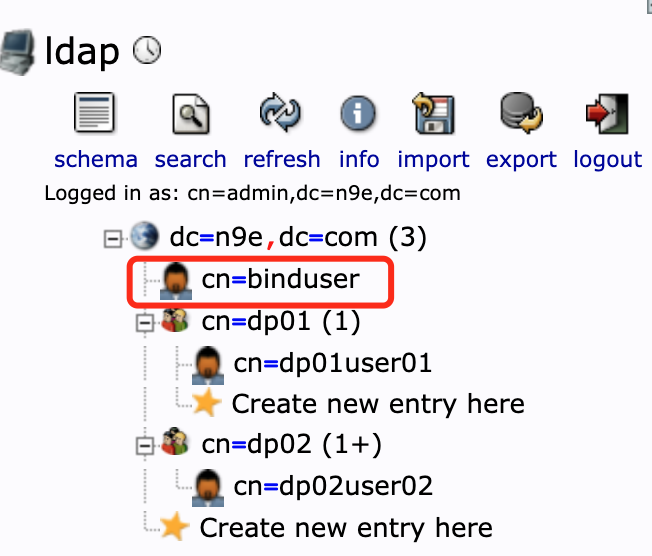
BindUser = 'cn=binduser,dc=n9e,dc=com' is the user DN used to bind to the LDAP server. This user needs sufficient permissions to search for users and verify credentials; (this user needs to be created in LDAP first and set permissions)
BindPass = '1234' is the password for the user binding to the LDAP server;
Below is a simple example of LDAP configuration for creating binduser and acl:
1. Create bind user file binduser.ldif
root@9a90f3b798ee:/# cat binduser.ldif
# Entry for bind user
# Note: Replace cn/dc related information
dn: cn=binduser,dc=n9e,dc=com
objectClass: inetOrgPerson
objectClass: posixAccount
cn: binduser
sn: Bind
uid: binduser
userPassword: 1234
uidNumber: 10000
gidNumber: 10000
homeDirectory: /home/binduser
2. Create bind user acl file
root@9a90f3b798ee:/# cat binduser-acl.ldif
# Add ACL for bind user
dn: olcDatabase={1}mdb,cn=config
changetype: modify
add: olcAccess
# Note: Replace dc/cn and other related information
olcAccess: to dn.subtree="dc=n9e,dc=com"
by dn.exact="cn=binduser,dc=n9e,dc=com" read
by * none
3. Create bind user, note to modify dc/cn information, fill in admin's password after -w parameter
ldapadd -x -D "cn=admin,dc=n9e,dc=com" -w 1234 -f binduser.ldif
4. Add bind user acl, note to modify dc/cn information, fill in admin's password after -w parameter
ldapmodify -x -D "cn=admin,dc=n9e,dc=com" -w 1234 -f binduser-acl.ldif
TLS = false option is true|false, enable according to LDAP settings.
StartTLS = false option is true|false, enable according to LDAP settings.
DefaultRoles = ['Guest'] sets the account permissions for LDAP accounts after logging into Nightingale, options are Admin/Standard/Guest;
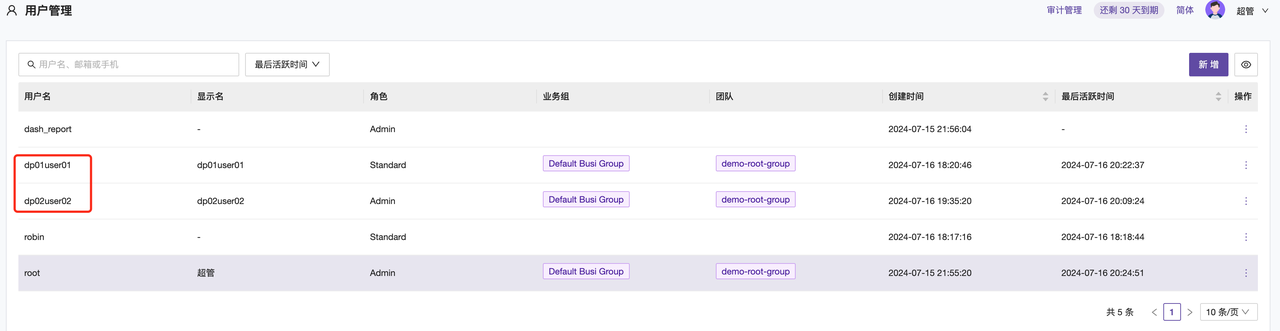
DefaultTeams = [21] sets the business group ID that LDAP accounts belong to after logging into Nightingale (as shown in the figure below);
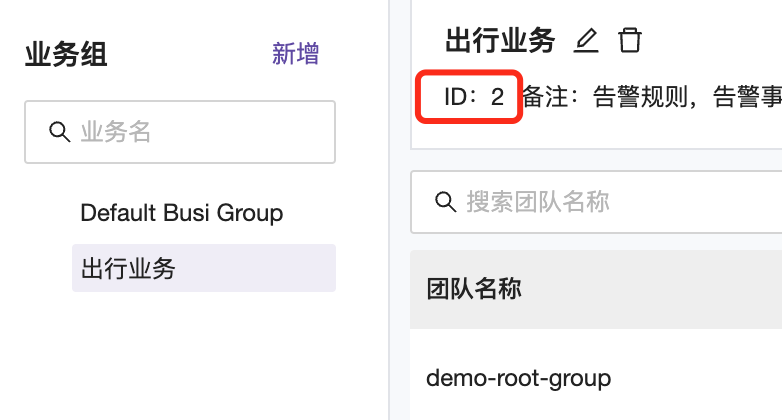
Other configurations can be kept default if there are no special needs. After modifying and saving the configuration information, you can test logging in with LDAP accounts.